Version 1.670
Released: 2024-11-06
Extended color customization evolution new
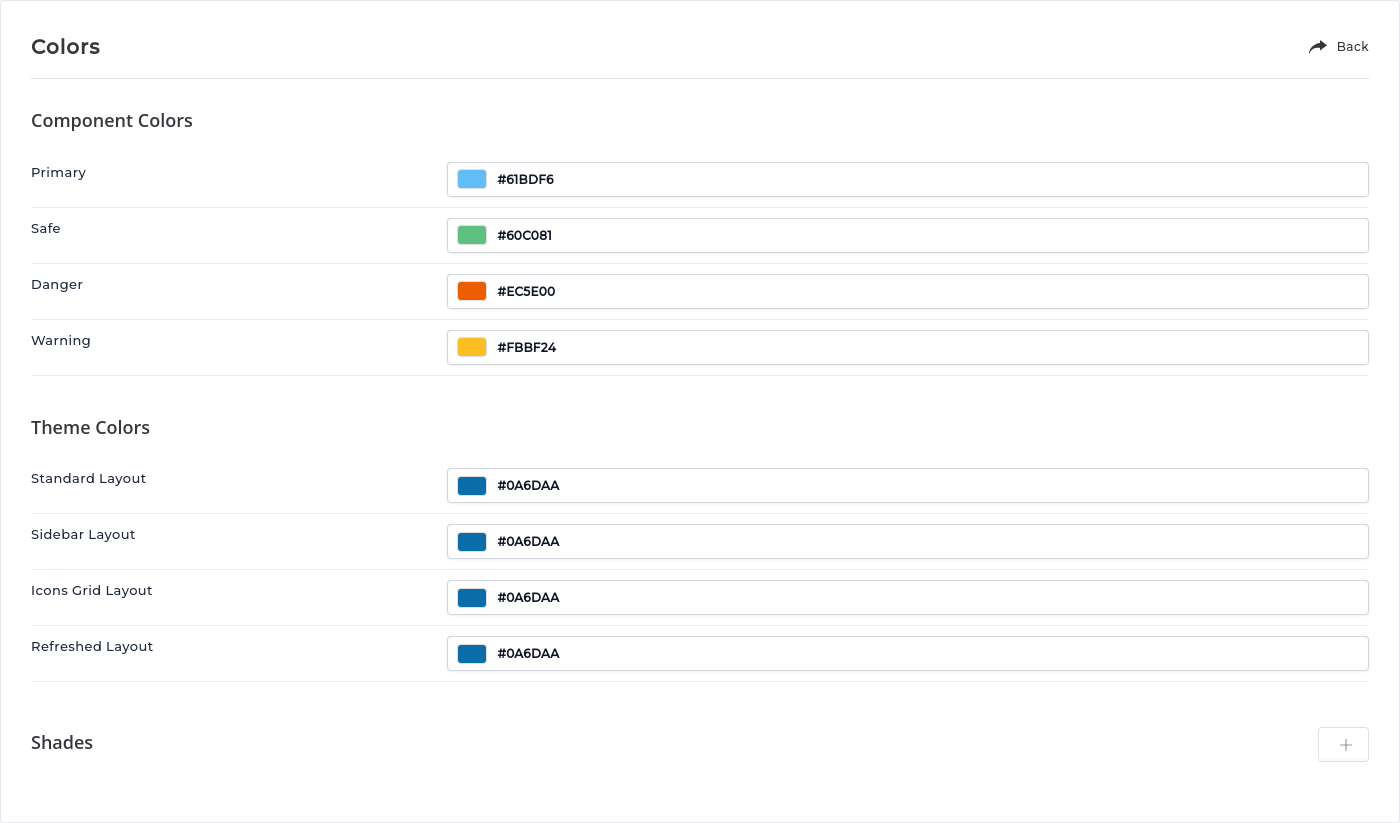
The Evolution skin colors customization page is extended to allow changing the main theme color for each layout separately. In previous releases, it was only possible to have one color for the Refreshed layout and one color for all other layouts.
It is now also possible to customize the color for warning elements.
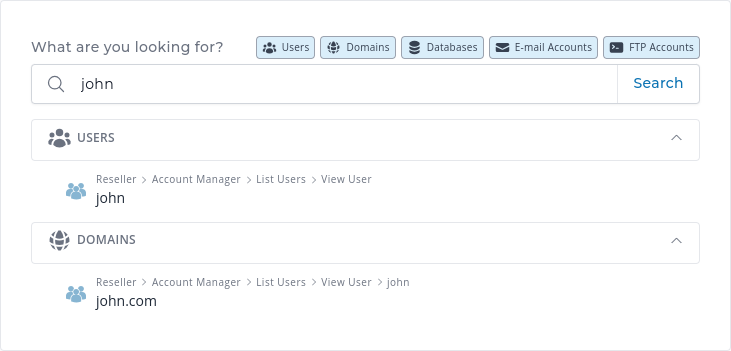
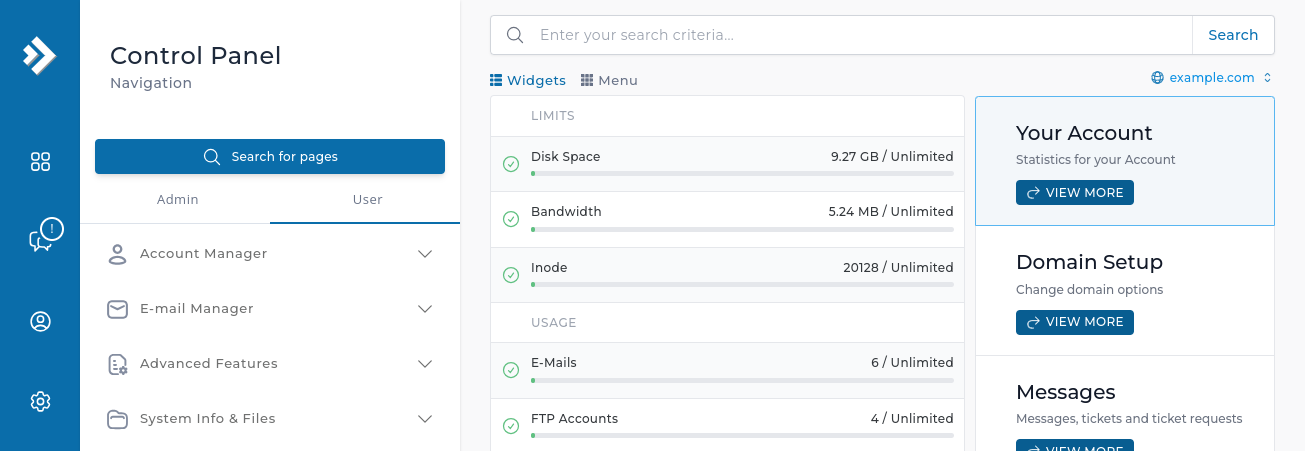
Separate page for global users, domains, etc. search evolution new
The search for users, domains, and other accounts on the server will be shown on a separate page dedicated for search results.
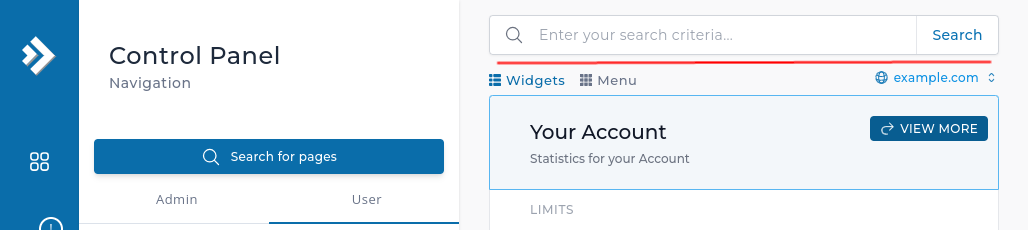
The search bar for backend search is now available in the dashboard for all of the layouts.
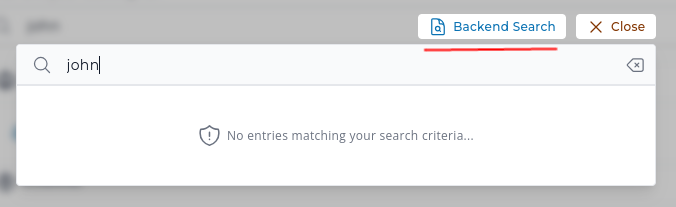
It is also possible to enter backend search mode from the quick page search window.
Icons Grid layout update evolution update
The Icons Grid layout received a big update. It now uses the main theme color for the page header. The navigation grid also uses theme color background for the menu groups.
These change make non-customized Icons Grid layout close to what used to be a "traditional" sub-theme. Adding the custom CSS rules for creating a "traditional" sub-theme is no longer needed.
![]()
Refreshed layout new theme color evolution update
The Refreshed layout will start using #0A6DAA blue as the default theme color. It is a darker shade of the previous default theme color and the same color as used in other themes. This change makes sure all supported layouts use the same default theme color, making different layouts have a more unified look.
In previous releases, the default Refreshed theme color was #61BDF6 (same as primary). It is easy to continue using the old lighter blue color by changing it in the skin color customizations page.
New config option user_area_locking=60 to allow disabling of area locking new
By default, the internal system has an "area locking", which prevents a User from making multiple actions on a given feature at the same time. This was previously not alterable, but in some cases it could be valid to disable it in cases such as slow systems that require a large amout of time for some of those actions. Of course, disabling the this feature is not recommended and will be at your own risk:
da config-set user_area_locking 0
systemctl restart directadmin
Related: Not to be confused with, user_action_locking=30 which is meant to lock the entire User to prevent races for backups, User creation, and User deletion.
Updated Pure-FTPd install and remove scripts update
The CustomBuild scripts for installing or removing Pure-FTPd received a major upgrade. Notable changes:
- Sources are now downloaded from upstream by default. This means new versions can be used even before sources are uploaded to DirectAdmin mirror servers.
- Source packages are cached and not re-downloaded every time the service is rebuilt.
- Compilation is performed in a temporary directory to make sure each build is clean and cannot be affected by failures of previous compilation attempts.
- Compiled Pure-FTPd binaries no longer includes debugging symbols.
- Removed old patches that are no longer relevant for modern systems.
- Removing pure-ftpd no longer requires downloading and configuring pure-ftpd sources for the removal action.
- The removal script has a more up-to-date file list to remove all no longer needed files.
Upgraded custom lost password page update
The lost password feature (available by navigating to /CMD_LOST_PASSWORD) uses Evolution skin by default. It is possible to use a custom lost password template by creating a new file in data/templates/custom/lost_password.html.
The lost password template is upgraded to allow showing success or error messages for the lost password action using the same template file. Previously, all success or error messages used to be shown on a blank page, which was not customizable.
The new template engine now supports the nested |*if...| expressions. This makes it easier to use the same template for showing error messages as well. An example of a custom lost password template can be found in the feature documentation.
Note: Existing customized pages need to be updated to start using the new |message| token. If not updated, the old templates will work but will not show the error or success messages.
Simpler two-step authentication UI for Enhanced skin update
Enhanced skin no longer uses JavaScript code to generate the Two-Step authentication setup QR code. The QR code is generated on the backend and sent to the client embedded in the HTML response.
Software version changes custombuild update
composerupdated from2.8.1to2.8.2dovecot-fts-xapianupdated from1.7.16to1.7.17ioncube_loadersupdated from13.3.1to14.0.0litespeedupdated from6.3.1-2to6.3.1-4MariaDB 10.11updated from10.11.9to10.11.10MariaDB 10.5updated from10.5.26to10.5.27MariaDB 10.6updated from10.6.19to10.6.20MariaDB 11.4updated from11.4.3to11.4.4modsecurity_owasp_rulesupdated from4.7.0to4.8.0MySQL 8.0updated from8.0.39to8.0.40MySQL 8.4updated from8.4.2to8.4.3openlitespeedupdated from1.8.1to1.8.2PHP 8.2updated from8.2.24to8.2.25PHP 8.3updated from8.3.12to8.3.13pureftpdupdated from1.0.51to1.0.52
Support older MariaDB versions on RHEL 9 based systems custombuild update
CustomBuild will support installing MariaDB 10.3, 10.4, and 10.5 on RHEL 9 systems. This ensures the same set of MariaDB releases are supported on all Linux distributions.
Added validation to SpamAssassin evolution update
SpamAssassin (located in user level -> E-mail Manager -> SpamAssassin Setup) form inputs now have validation.
Allow USERNAME and CREATOR tokens in the 3rd party ticket system URL update
When they've disabled the ticket system for their Users, Admins and Resellers can now use tokens in their Manage Tickets area (/evo/reseller/tickets), under the Ticket System Settings popup. When the Ticket System Enabled checkbox is unchecked, they'll be allowed to use:
|USERNAME|
|CREATOR|
in their URL, as needed. This is useful if they require to include who is creating the ticket when they're being redirected to the 3rd party ticket system. Note, these values are only for convenience, and enforcement the value should not be entirely trusted as the User could just paste any other value that they wish when accessing the URL. Related: CMD_TICKET_MANAGE will return the "raw" un-tokenized value, but when Users refer to the URL (CMD_TICKET_CREATE), it will be tokenized.
DEFAULT CHANGE: convert_to_punycode=1 update
Improved checks on UTF-8 domains and subdomains are now fully enforced. As a result, it's simplest to automatically convert non-punycode domains into punycode where needed. The Evolution skin already converted domains before submitting to DA, but API calls and other skins might not have. This means that any domain with UTF-8 characters (or any ASCII greater than 127), will now always be converted into punycode. Any domain or subdomain already created in DA will not be affectd. Only new domains or subdomains will have this enforcement. Backup/Restores will also not be affected/enforced.
If needed, this can be disabled using:
da config-set convert_to_puncycode 0
systemctl restart directadmin
Flexible Restore filename format update
The Admin/Reseller Level restores are now more flexible in the backup file naming. New formats allow for extra 'chunks', separated by dots. As before, there are 2 formats:
Reseller: containing just the Username, created by Resellers
Admin: contains the type, creator, and Username, created by Admins
The backups created by Users are not affected.
The Reseller format, can now be restored with either:
fred.tar.zst
fred.CHUNK.tar.zst
while the Admin format can now allow:
user.admin.fred.tar.zst
user.admin.fred.CHUNK.tar.zst
user.admin.fred.CHUNK.CHUNK.tar.zst
Where CHUNK can be any simple text value, as long as it does not contain a dot, which is the chunk separator. The Admin format allows as many CHUNKs as desired, eg: user.admin.fred.2024-10-23.MD5_123ABC.tar.zst.
As before, the tar.zst extension can be any of:
tar
tar.enc
tar.gz
tar.gz.enc
tar.zst
tar.zst.enc
Related:
- user_backup_post, user_backup_success to rename the local file as needed.*
- custom ftp_upload.php to create a custom copy to rename the file as it's being uploaded.*
Enhanced two-step authentication rework update
Following two-step authentication page refresh in Evolution, CMD_TWOSTEP_AUTH page is updated.
Key changes:
- removed
/CMD_API_TWOSTEP_AUTH. It has been replaced with/api/multi-factor-auth/endpoints - removed
/CMD_TWOSTEP_AUTH?action=untrust. - removed
/CMD_TWOSTEP_AUTH?action=select&delete=... - removed
/CMD_TWOSTEP_AUTH?print=scratch_codes /CMD_TWOSTEP_AUTH?action=testno longer acceptsmultipart/form-data/CMD_TWOSTEP_AUTH?action=testno longer checks for time discrepancy between client and server/CMD_TWOSTEP_AUTH?action=testnon json response returnsHTM_INDEXtemplated result instead of simple html snippet./CMD_TWOSTEP_AUTH?action=select&add=...recreates scrach codes instead of adding them/CMD_TWOSTEP_AUTH?action=settingsno longer acceptstwostep_auth_description- Removed description field and always hidden untrust form
Deprecated tokens:
SPACED_SECRET(useSECRET)KEY_NAME(always empty, otp secred description no longer customizable)MAX_ATTEMPTS(always0: due to removedmax_twostep_auth_attemptsdirectadmin.conf option)TWOSTEP_TRUSTED_DEVICE(alwaysno. otp trust cookie no longer send when accessingCMD_TWOSTEP_AUTH)
Removed terms from twostep_auth lang file:
LANG_DESCRIPTIONLANG_DESC_IN_PHONELANG_CURRENTLY_TRUSTEDLANG_REMOVE_TRUSTLANG_REMOVE_TRUST_EXPLANATIONLANG_NOTIFY_ME(replaced withLANG_NOTIFY_ON_FAILURES)LANG_FAILED_ATTEMPTS
Response info in access log update
Access log file (located /var/log/directadmin/access.log) is extended to have response status code and response body size.
Updated access.log format:
[time in RFC3339] [processing time in sec] [client address] [status code] [response size in bytes] [method] [path] [referer/origin] [auth user] [auth type] [auth id]
Example:
2024-10-30T00:00:00Z 0.010 127.0.0.1 200 1522 GET /api/db-show/databases https://test.directadmin.dev:2222/evo/user/database admin session-native -
Looser database naming validation update
Database name and database user names can only contain alphanumerical, underscore and hyphen characters. Previously a restriction was set that name cannot start or begin with an underscore or hyphen.
Validation is updated to allow to use underscores and hyphens in any position. One exception being, database user name cannot start with an underscore, i. e., cannot contain double underscores after DA username. E. g., admin__dbuser is not allowed.
Enforce skin customization option for forbidding layout changing evolution fix
Within layout customizations page (located in Admin Tools -> Customize Evolution Skin -> Layout) the "Forbid users changing the skin layout on user level" option was ignored when regular users attempted to change their layout within the Skin Options page.
Disabled menu entries in reseller level affected admin level counterparts evolution fix
Certain menu entries when disabled in reseller level also were unavailable within the admin level. This was the case for the following pages:
- "Add New User"
- "List Users"
- "Manage User Packages"
- "Edit User Message"
- "Name Servers"
- "Security.txt Report"
- "cPanel Import"
- "Message All Users"
- "Skin Manager"
- "Customize Evolution Skin"
- "Manage Tickets"
- "Create Tickets"
Domain pointer removal blocked by pre-hook shows successfull removal message fix
If domain pointer removal is blocked by the pre-hook domain_pointer_destroy_pre.sh script, the removal failure message used to be styled like the action was successful (green message box).
The issue is fixed. The domain pointer removal message will be styled as a failure (red message box) if the pre-hook script blocks its removal.
Crash on user suspension if FTP config files are locked fix
A bug is fixed that caused a single request handler to crash if the user account is being suspended but the FTP password file is locked for making changes by another process.
Jailshell on Ubuntu 24 with apparmor fix
Ubuntu 24 release has a default AppArmor policy of blocking applications that create user namespaces. The jailshell uses this feature and gets blocked by apparmor.
The jailshell installation script is updated to add the AppArmor profile that allows jailshell to run.
Fix ModSecurity rules ranges fix
Using ModSecurity with nginx or openlitespeed web servers used to fail in case a range of rules were disabled, e. g., SecRuleRemoveById "1234-1239". This was caused due to quotes surrounding the range.
Rules disabling is updated by dropping the quotes for ranges. Currently existing ranges can be manually migrated by recreating them without quotes.
Example: SecRuleRemoveById 1234-1239.
Fixed Litespeed >= 6.3 error logging custombuild fix
Previously during PHP rebuilds custombuild would change <logLevel>DEBUG</logLevel> to <logLevel>ERROR</logLevel> in /usr/local/lsws/conf/httpd_config.xml.
Due to recent changes in Litespped this custombuild change introduces a bug resulting in domain error logs at /var/log/httpd/domains being empty.
It is advised to check your /usr/local/lsws/conf/httpd_config.xml and if <logLevel>ERROR</logLevel> is present revert it to <logLevel>DEBUG</logLevel>.
Fixed LiteSpeed management URL in Extra Features custombuild fix
CustomBuild was failing to create index.html in plugins folder, thus LiteSpeed management URL was not shown in Extra Features. CustomBuild regression was fixed.
Removed pipe_log configuration option from directadmin.conf removal
The configuration option pipe_log is used to specify a file where all the stdout and stderr messages from taskq actions are redirected. This configuration option is removed. The output will always go to stdout and stderr.
The messages printed when executing taskq actions will now be visible in the main directadmin service journal. It can be checked with the journalctl -u directadmin command.
Removed twostep_auth_description user configuration option removal
Account name in Two-step authentication provisioning URI is no longer modifiable and will always be set to username.
Removed legacy request log files /var/log/directadmin/YYYY-Mon-DD.log removal
The log files /var/log/directadmin/YYYY-Mon-DD.log will no longer be created. They are superseded by the more verbose access log file /var/log/directadmin/access.log.
